Understanding, Implementing and Profiting from NIS-2

Cybersecurity has become a strategic necessity. With the enactment of the NIS2 Implementation and Cybersecurity Strengthening Act (NIS2UmsuCG) on December 6, 2025, stricter standards now apply to a wide range of companies in Germany, regardless of industry or size. More businesses are affected, the requirements for organization, risk management, and IT security are more comprehensive, and the consequences for non-compliance are considerably tougher. Affected organizations must act immediately: there is no transition period, and registration with the BSI is mandatory for companies within three months. The responsibility lies directly with the management.
For medium-sized companies in particular, this means that you must review your processes, systems and responsibilities. NIS-2 not only obligates you to implement technical protective measures, but also to ensure clear organizational responsibilities, risk management and complete documentation at the organizational level. With smart process management and modern BPM software like Bpanda, you can strengthen your structures, meet legal NIS-2 requirements, and build long-term trust with your customers and partners.
Is Your Company Affected?
If you are responsible for processes, compliance or IT security in your company – for example as a quality manager, process manager, compliance officer, IT security manager, IT manager or CISO – you will soon no longer be able to ignore the NIS-2 directive. This is because NIS-2 no longer only affects large corporations or conventional critical infrastructure providers – the scope has been significantly expanded. Medium-sized companies that provide so-called essential or important services are now also under obligation. Now is the right time to check whether your company is affected and what your obligations are.
You should be proactive if your company falls under the following criteria:
![]() Your company employs more than 50 employees or generates more than 10 million Euros in annual revenue.
Your company employs more than 50 employees or generates more than 10 million Euros in annual revenue.
![]() Your company is active in one of the sectors concerned (e.g. healthcare, water, digital infrastructure & telecommunications, energy, transport, finance, insurance, waste management, food production or industrial manufacturing).
Your company is active in one of the sectors concerned (e.g. healthcare, water, digital infrastructure & telecommunications, energy, transport, finance, insurance, waste management, food production or industrial manufacturing).
![]() Your company is part of a critical supply chain or a service provider for critical infrastructure operators.
Your company is part of a critical supply chain or a service provider for critical infrastructure operators.
What does This Mean for Your Role within Your Company?

Process Manager or QA Manager
You need to establish stable and traceable processes in the company. NIS-2 requires robust and clearly documented processes for risk assessments, security incidents, escalations and the involvement of external service providers. With a professional BPM approach, you lay the foundation for transparency and traceability.

Compliance Manager
You are responsible for ensuring that legal requirements are systematically integrated into the organization and complied with. NIS-2 requires not only proof of existing protective measures, but also regular review of these measures, clearly defined responsibilities and revision safety documentation.

IT Security Manager, CISO or IT Manager
You are faced with the challenge of defining, implementing and continuously reviewing technical and organizational security measures. The requirements for risk management, access security, backup strategies and response plans are increasing noticeably – as is personal accountability in the event of an incident.
NIS-2 Challenges at a Glance
NIS-2 significantly increases both technical and organizational demands on companies. Those affected must take action.
Implement and Certify Cyber Security MeasuresYou are obligated to implement technical and organizational measures for IT security – including access controls, vulnerability management and emergency plans. These need to be regularly reviewed and documented.
Obligation to Report Security Incidents You must report security incidents to the responsible authority within 24 hours. Detailed follow-up reports are then required. This requires not only clear processes, but also rapid coordination and documented responsibilities.
Define Clear ResponsibilitiesNIS-2 requires clear responsibilities up to management level. Cyber security is not the sole responsibility of the IT department; it is becoming managerial responsibility and must be firmly established in organizational, technical and procedural terms.
Audits & Inspections by Authorities National authorities may carry out unannounced inspections in future. Companies must be able to prove the implementation and effectiveness of their security measures at any time – in writing, traceable and audit-proof.
Why Process Management is the Key to NIS-2 Compliance
An effective approach to fulfilling NIS-2 requirements is the introduction of business process management (BPM). BPM enables you to visualize and analyze your business processes and make improvements where necessary. This not only creates transparency regarding security-relevant processes, but also ensures the efficient and traceable fulfillment of regulatory requirements. BPM lays the foundation for a sustainable security architecture with audit capabilities – not just for today, but also for future regulations.
Clear processes for security incidents, prevention and escalation
Structured process documentation as proof for authorities
Link with risk management to control vulnerabilities
Clear role assignment and responsibilities in black and white
Automated verification and release processes
Continuous improvement thanks to measurable process ratios
Bpanda – Your BPM Tool for NIS-2 Implementation
Bpanda is a modern, intuitive BPM tool perfect for complying with NIS requirements. Bpanda can help with central, structured and traceable documentation of your business processes, to control risks and set clear responsibilities. MID GmbH is the software provider behind Bpanda; a German software and consultancy company with over 40 years experience in process management. GDPR-compliant and certified development and hosting takes place exclusively in Germany.
Transparent Process Landscape
Bpanda helps you to easily model and document all safety-relevant processes so they can be understood by everyone involved. This gives you a clear overview of where risks could arise and where you may need to take action.
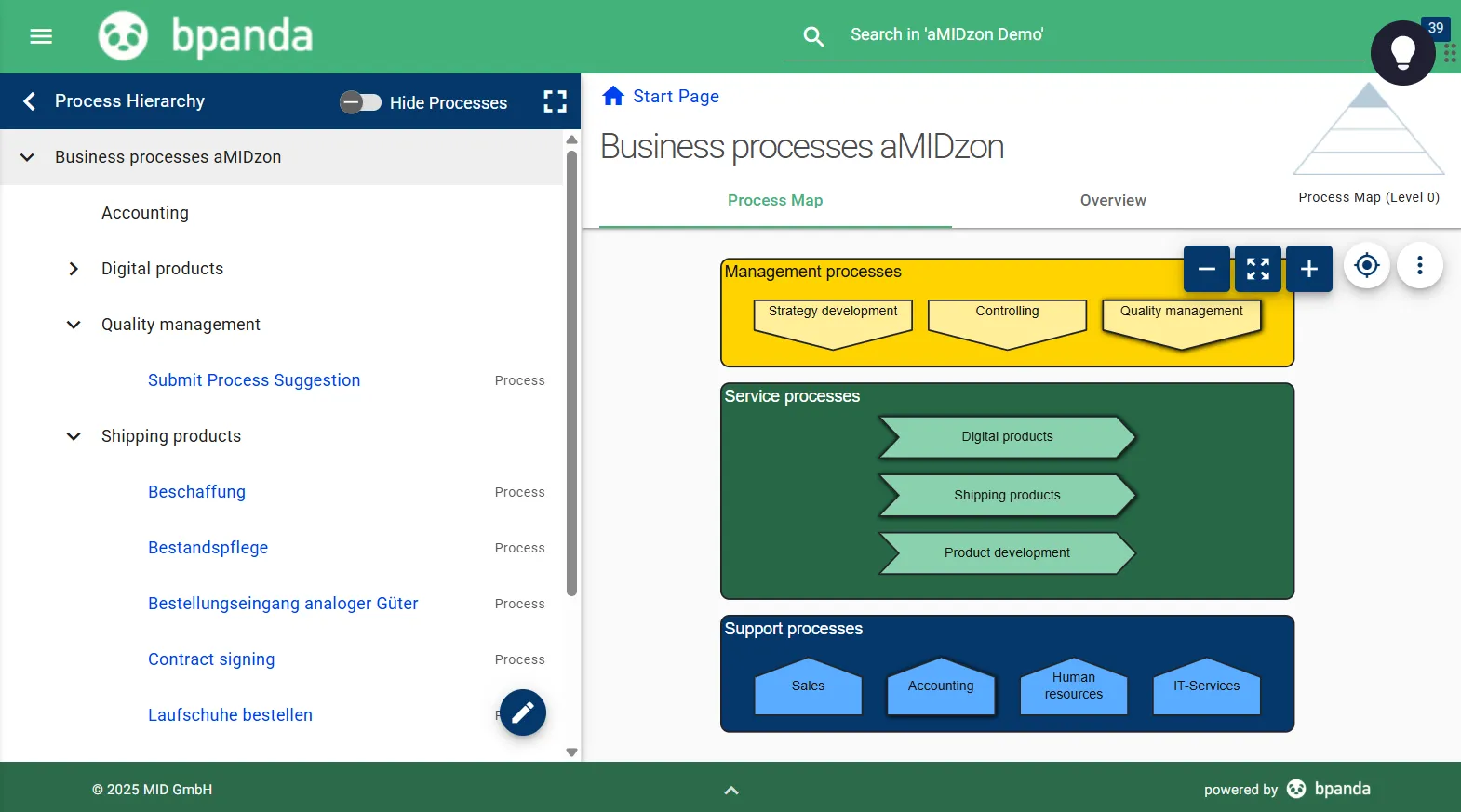
Revision Safety Documentation
All processes are automatically versioned and saved so they can be traced. Changes and responsibilities are seamlessly documented, which is a key factor for audits and authority checks.
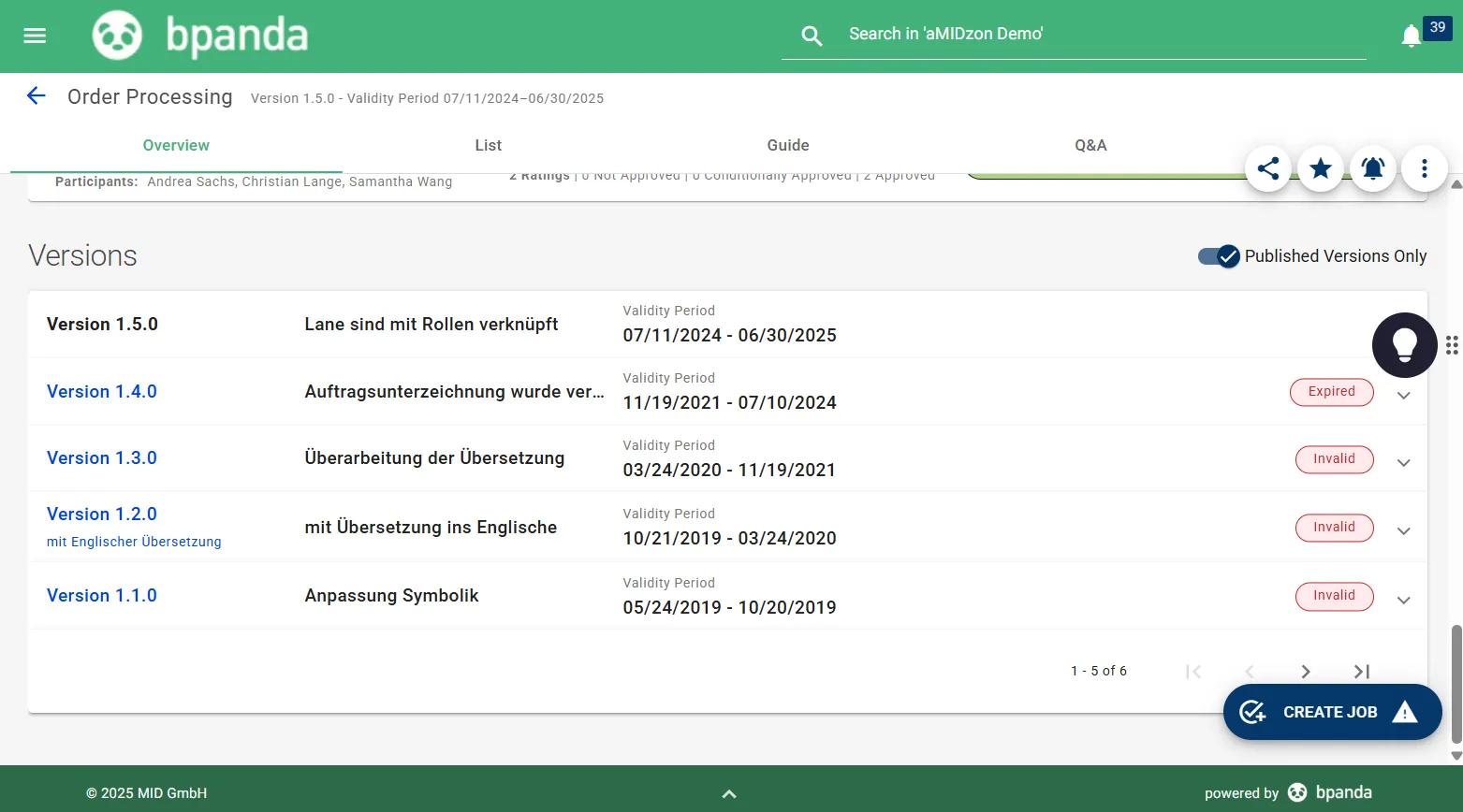
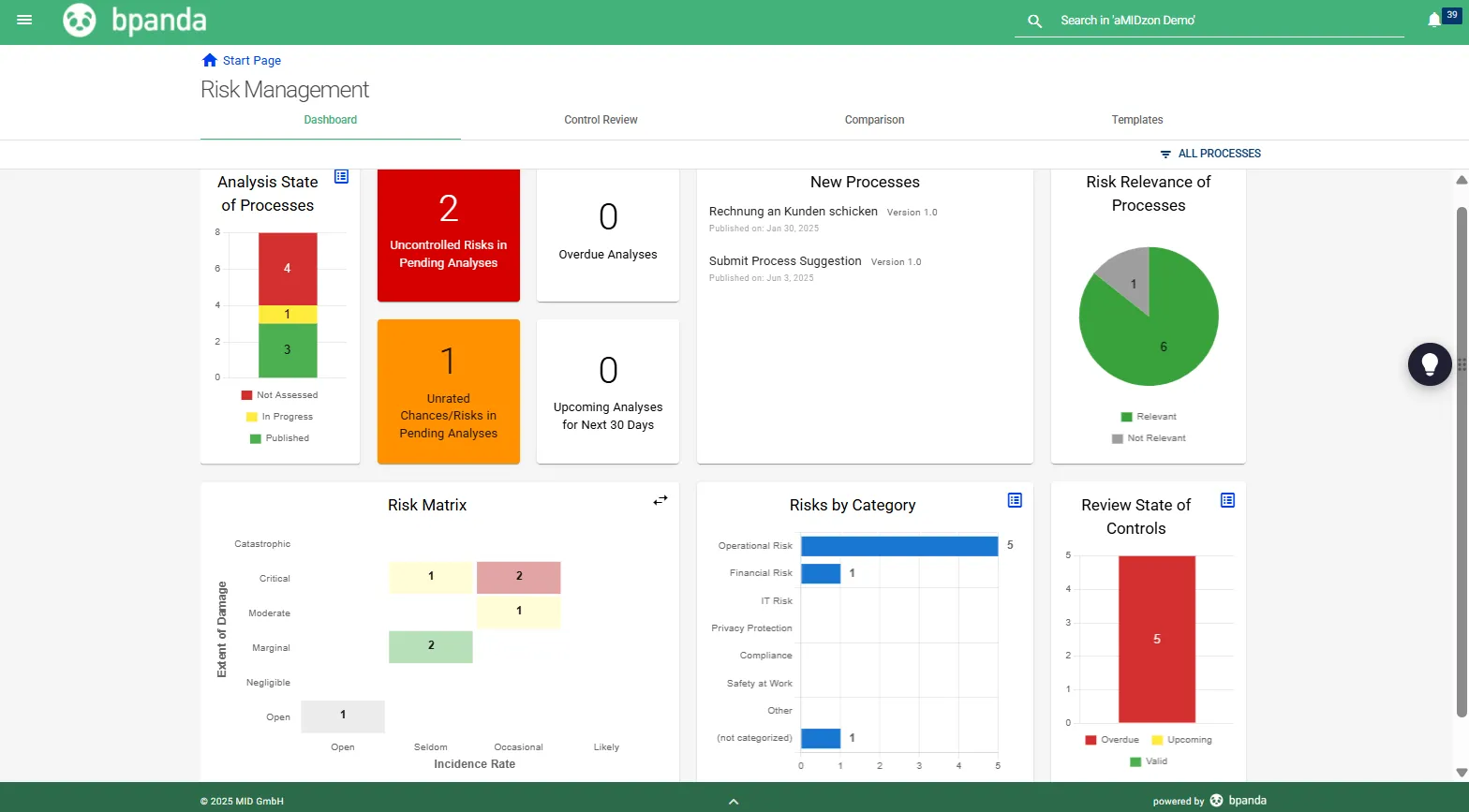
Practical Risk Management Integration of Processes and Risks
Bpanda enables direct linking of processes to identified risks and necessary security measures. Actively control your risk management and satisfy your NIS-2 obligations in the long term.
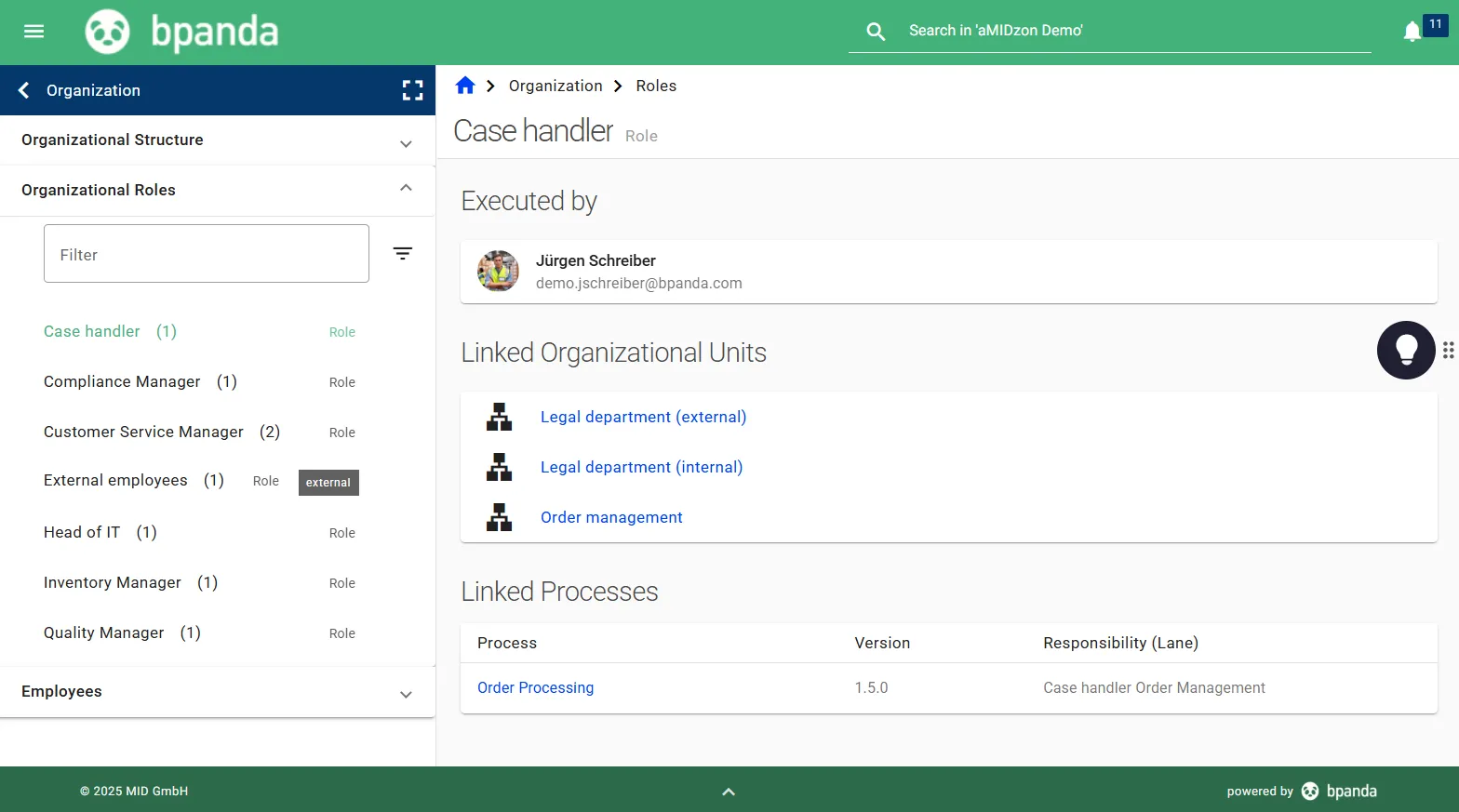
Stored Responsibilities: Clearly-Defined Roles and Responsibilities
Use Bpanda to assign roles, tasks and releases at both a process level and within your company. This allows the legal requirement of responsibilities at a management level to be effectively monitored.
Intuitive and Easy to Use: Simple Rollout and Acceptance
Thanks to its user-friendly interface, Bpanda can be used straight-away, without previous knowledge of BPM. This considerably speeds up implementation of NIS-2 measures.
Recognizing and Analyzing Dependencies
Bpanda gives you an overview of how processes, roles, IT systems and risks are linked with each other. This enables you to identify dependencies in good time and take targeted counter measures. This helps you to fully understand vulnerabilities and to take safety measures in the right areas, especially in the context of NIS-2.
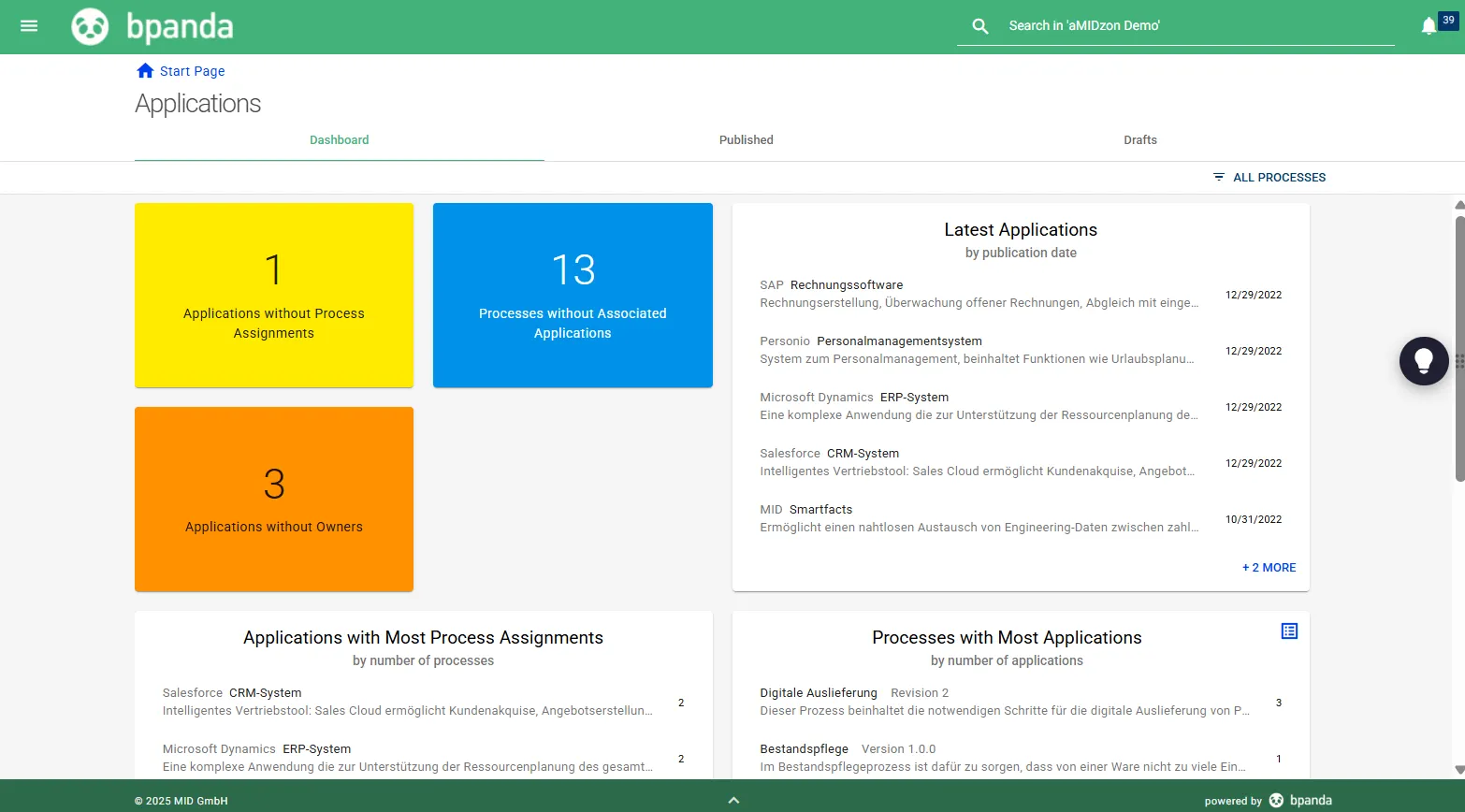
Your NIS-2 Guide: Compact, Clear, Practical
Download Now for Free
Get the compact guide for a successful NIS-2 implementation with BPM! Learn how to make your processes and responsibilities ready for the new requirements.
What you can expect:
- Overview of NIS-2 challenges
- Step-by-step instructions
- Concrete implementation tips in Bpanda
Simply fill out the form and download the guide as a PDF directly!
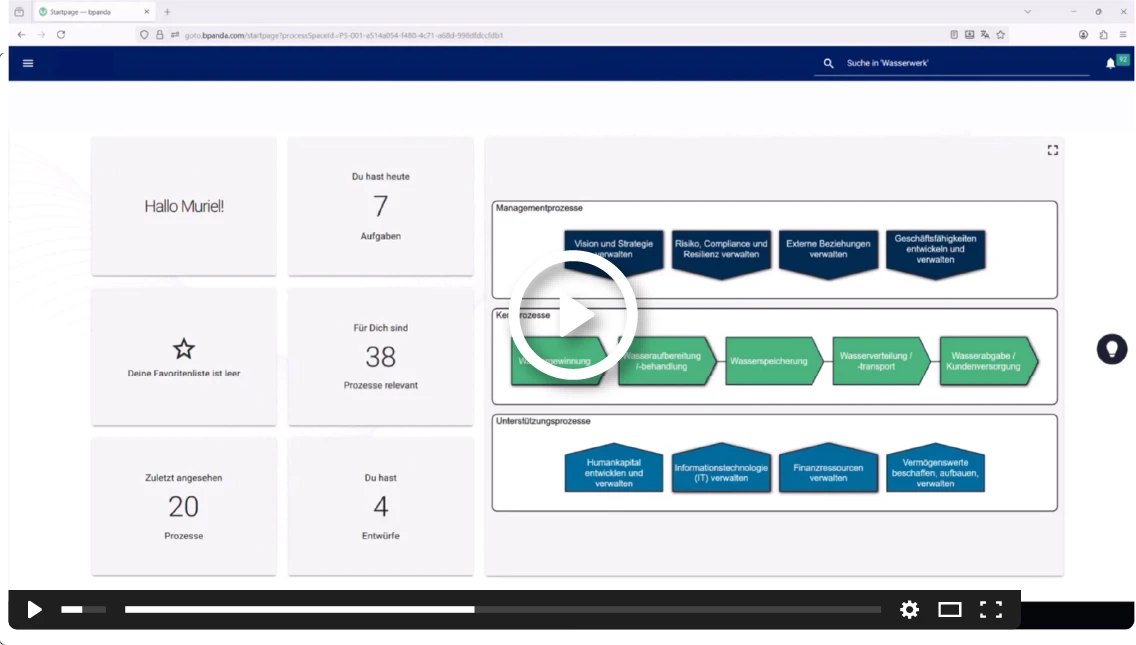
Exclusive NIS-2 Demo:
How to Implement the Requirements with Bpanda
In our short 8-minute demo video, we’ll show you step by step how to define responsibilities in Bpanda, model your processes, manage risks, and document reporting obligations — all using a practical example from a water utility company. Curious? Just fill out the form and watch the demo video for free. Take your organization’s NIS-2 implementation to the next level!
Start Today – Try Bpanda Now for Free!
Do you want to see what BPM is like in practice? Test our lightweight and web-based process management tool, Bpanda, for 30 days – it’s free, non-binding and no installation required. Create, share and optimize processes as a team. It’s the perfect tool for getting your organization up to scratch for NIS-2.
![]() GDPR-compliant, made & hosted in Germany
GDPR-compliant, made & hosted in Germany
![]() Ideal for specialized departments, IT and compliance
Ideal for specialized departments, IT and compliance
![]() Instant trial access with no IT set-up
Instant trial access with no IT set-up
Start Today – Try Bpanda Now for Free!
Do you want to see what BPM is like in practice? Test our lightweight and web-based process management tool, Bpanda, for 30 days – it’s free, non-binding and no installation required. Create, share and optimize processes as a team. It’s the perfect tool for getting your organization up to scratch for NIS-2.
![]() GDPR-compliant, made & hosted in Germany
GDPR-compliant, made & hosted in Germany
![]() Ideal for specialized departments, IT and compliance
Ideal for specialized departments, IT and compliance
![]() Instant trial access with no IT set-up
Instant trial access with no IT set-up
Put Your Trust in Certified Safety – Made in Germany
What counts when it comes to cyber security? Trust. As an SaaS provider with the highest quality and security standards, we ensure your sensitive data is protected to the highest level and is fully GDPR-compliant. Bpanda is not simply a powerful BPM tool – it is also created by a provider who lives and breathes security, quality and transparency. You can count on us:
ISO 9001 & TISAX certified: MID GmbH fulfills international standards for quality management and information security.
100,000+ active users believe in Bpanda as the right BPM tool for their company. Awarded first place at the Process Solution Awards.
Secure infrastructure: Bpanda is developed in Germany and hosted in the secure IONOS Cloud (ISO 27001, ISO 9001, ISO 14001, BSI C5).
Member of the Alliance for Cyber Security: We are an active member of the alliance, working together with other companies to make a strong digital Europe.
ISO 9001 & TISAX certified: MID GmbH fulfills international standards for quality management and information security.
100,000+ active users believe in Bpanda as the right BPM tool for their company. Awarded first place at the Process Solution Awards.
Secure infrastructure: Bpanda is developed in Germany and hosted in the secure IONOS Cloud (ISO 27001, ISO 9001, ISO 14001, BSI C5).
Member of the Alliance for Cyber Security: We are an active member of the alliance, working together with other companies to make a strong digital Europe.
Frequently Asked Questions
The NIS2UmsuCG came into force on December 6, 2025. All requirements apply immediately; there is no transition period. Affected businesses and organizations must register with the BSI within three months – that is, no later than March 6, 2026. Additional obligations, such as risk management, reporting, and documentation requirements, must also be implemented from the effective date.
Fines of several million and managers also face personal liability. Security issues and inspections by authorities may also lead to loss of image.
NIS-2 requires a risk management for IT systems, measures for access controls, back-up concepts, security checks and a back-up plan, to name but a few. These measures must be documented and regularly checked.
NIS-2 goes significantly beyond the previous KRITIS regulation. It affects more sectors, has more stringent registration deadlines and stricter requirements, e.g. a clear assignment of responsibility, right the way through to management level.
Yes – complete documentation is mandatory. Authorities may request proof of implementation of protective measures or reaction to security issues. Well-documented processes are the best basis for this.
Process management helps you to systematically implement organizational requirements set-out in the NIS-2 directive. A BPM tool such as Bpanda allows you to document security processes, define responsibilities and ensures that reaction flows are clearly defined and can be traced.
Bpanda enables you to centrally document processes, link them with roles and trace them using versions. This allows you to efficiently map technical and organizational measures and gives you quick access to all relevant information for audits or security incidents.
A digital and central process documentation is highly recommended; not only as an obligation of proof, but also for quicker reaction capabilities in case of an emergency. It’s easy with Bpanda and there is no need for complex tools; you can work directly from the browser.
There is no fixed period, but processes should be regularly checked, up-dated and changed straight away if an emergency arises. Continuous process maintenance is part and parcel when it comes to a security concept. Bpanda can provide straight-forward and audit-proof support for you.
Whether IT management, CISO, compliance or quality assurance, Bpanda provides a common platform for defining, communicating and implementing cyber security processes across all departments. Transparent collaboration for all involved – even those without IT experience.